(Minghui.org) Note: This training material is intended for practitioners outside of mainland China. Practitioners in mainland China can use this as a reference for general principles but some portions might not apply.
Table of Contents
General GuidelinesCommon Attack VectorsRemove WeChat, TikTok, and Similar Apps from the Primary DeviceTurn off Devices and Put Them Away for Sensitive DiscussionsDirect Online AttacksOnline Phishing AttacksMonitor Email Access SummaryKeep Your Devices up to DateStandard User for Most Activities on DevicesOnly Run Trusted ApplicationsProtect Data on Devices with Passcode, Encryption, and BackupGeneral Technical DetailsData BackupProtect Data with EncryptionUse a Password ManagerEmail Client SetupOther MeasuresMobile DevicesMac OSNetwork configurationsWindowsNetwork ConfigurationsWindows 11 Security Features
General Guidelines
Common Attack Vectors
This training material is intended to help improve your understanding of information security and establish best practices. Please take the time to study and understand this material, and implement the best practices as much as possible. This is not something you should skim once and put away. Please read it a few times to make sure you understand everything.
Let’s start with a story to illustrate some typical security failures. It would be obvious to see why certain security practices are necessary.
David managed to escape from China and arrived at a U.S. airport. He looked up the practice sites in this city and called John for help.
John picked David up from the airport and David stayed at John’s home for a few days before moving to a rental place. John and David discussed many things in the meantime, including the persecution David suffered in China and David’s plan to settle in the U.S. David used John’s home Wi-Fi network to access the Internet through his cell phone.
David created a contact for John on his phone and added more details. The practice site listed only John’s phone number and first name. David then added John’s last name and Chinese name. Since David would come back to John’s home again in the future he added John’s home address to the contact details. For the residence application there is a need to use email to exchange documents so David added John’s email to the contact details and started to use email to communicate with John.
John brought David to the group sharing place to see other practitioners, and David added more contacts.
After some time David was given a secure email and the secure email was added to the local group email list. David then started to see the email messages from many different practitioners on various projects. David started to see the roles of different practitioners and he diligently added the information to the details of the contacts. For example John hosts group sharing from time to time. David figured that John must be a coordinator or even an FXH assistant. Helen talked about various projects at the end of every group sharing. David figured that Helen might be an FXH member. He diligently marked John as an FXH assistant and Helen as an FXH member in his contacts.
John received an email message in his secure email advising him to change the password using a link in the email. The email looked like it was from the email system administrator. He opened the link and the web page looked familiar. The page asked him to enter his current password first and then the new password twice. He did it. He felt a little odd as he was still able to access his email on his phone without changing the saved password.
Later David received an email from John with an attachment titled “List of documents needed for residence application.” David felt a little odd as he had not asked for it. Since they talked about the residence application earlier it was not too odd. He opened it, as he trusted John. David noticed a little delay while the document was being opened. He thought his computer might be getting old, and moved on.
John later received an email from David’s secure email with an attachment titled “My stories of persecution in China.” John felt a little odd as he had not asked David for such a write-up. But since John and David talked about his persecution in China before and such a document is needed for the residence application it was not totally unexpected. John opened the document. It was indeed the story of David as published in Minghui earlier. John felt a little odd as there was a subtle hesitation when the document was opened. John brushed off the unease feeling and moved on.
Later John’s home was broken into. Laptops, USB thumb drives, and external hard drives were stolen, with project source code, server access passwords, and keys, and a presentation on future projects.
This is not the end of the story but we can stop here to count how many security failures occurred and what we can do to prevent these from happening.
Remove WeChat, TikTok, and Similar Apps from the Primary Device
Apps from China (including WeChat, TikTok, etc.) collect a lot of personal information from the device, including the details of all the contacts stored on the device. The evil has no trouble getting the collected information from the app makers. Precisely due to this lack of privacy protection, these apps pose significant security risks to us (a group targeted by the evil for persecution).
Upon the first run, WeChat will request permission to access the contacts on the device. It will quit immediately if the requested permission is not granted. If you can subsequently use WeChat you have granted WeChat the permission to access your contacts, regardless whether you understand the implications or not.
If David is on the blacklist and has WeChat on his phone, all the contact details he diligently added to his phone since the airport pickup would have been taken by WeChat and ended up in the hands of the evil. All the contacts he created for practitioners would have been sent to the evil via WeChat, including John’s last name, John’s Chinese name, John’s home address, email address, role, etc. Since David used John’s home Wi-Fi on his phone, WeChat servers would have recorded the IP address of John’s home network.
The evil was therefore able to send a phishing email to John’s email address. The evil could also attack John’s home network and devices since they had his IP address. If the phishing attacks and direct network attacks failed, the evil would still be able to launch physical attacks, including breaking into John’s home to steal laptops and hard drives. The evil would also be able to harass John’s family members in China.
If John had explained the danger of WeChat to David at the airport, and David had removed WeChat from his phone immediately, the story would have stopped right there.
We need to request that all practitioners remove WeChat, TikTok, and similar apps from China from their primary devices (phones, tablets, and computers). If you have to use these apps, use them on a separate device that has no contacts for practitioners.
Turn Off Devices and Put Them Away for Sensitive Discussions
Devices can also be used for eavesdropping when compromised. Turn off the devices and put them away during sensitive discussions. The discussions, if captured by the evil, can be used in social engineering attacks (e.g., the file names of the attachments in the story were related to the discussions John and David had before, making it very hard to avoid the trap).
Direct Online Attacks
The evil could obtain the IP address of a WeChat user. The IP could be the IP of the user’s home network, the IP of the media group’s office network, or the IP of the group sharing place. The IP will be recorded by the WeChat servers wherever the device goes while WeChat is running. The evil could carry out online attacks targeting the devices with the known IPs.
Our defenses against this type of attack: Turn on the firewall and keep all devices up to date with all the available security patches. The devices include computers and mobile devices on the internal network, as well as the gateway router.
Online Phishing Attacks
Phishing attacks are carried out through carefully crafted email messages and text messages which can deceive and mislead the targeted user, prompting them to perform device operations that would compromise the device. For example, the email might look like a system-generated email asking the user to change a password using the link in the email, while the link is controlled by the evil. The evil would capture the password if the user falls into this trap. For example, the email might look like it was from a known person but have a malicious attachment. Many file types could contain malware, including Word, Excel, PDFs, etc. For example, the email might contain a link to a malicious web page. Visiting the malicious page might cause some malware to be installed on the device. QR codes can also lead to malicious web pages. If the evil knows more about the target, such as the current hot topics of concern, relationships to other people, past conversations, etc., these details can be used by the evil to create social engineering traps. More details, more deceiving.
In the story, the evil obtained John’s email address and sent a phishing email to John asking him to “change password” via a link in the email. Why is this type of email deceiving? Because it exploits a behavioral characteristic of an email system.
Your email system may remind you that your password is about to expire. The evil is exploiting this behavior.
It is easy to avoid this trap if you stick to a simple rule. Once you see the password reminder, go to the webmail page to change your password, rather than clicking on a link in the email message. The same rule applies to any regular email accounts. You go to the webmail page (Gmail, Hotmail, etc.), then log in and change the password from there.
Never use links in email messages to change your password. The link could be controlled by the evil.
More generally, do not open links in emails unless you are sure the link is safe to open.
Let’s assume John failed this test and used the link in the email to change his password. The web page in the link was controlled by the evil and it would capture John’s current password in the first box. Since the web page was not linked to a practitioner-run project email server, John’s password on the email server was not changed. The evil would be able to log in to John’s email and setup a forwarding rule. From this point on all messages received by John would also be received by the evil, leaking a lot of information. The forwarding rule would continue to work even if John changes his password in the future, as long as the forwarding rule remains in place.
Monitor Email Access Summary
Once the evil gets John’s email password it would log in to John’s email account to set up a forwarding rule. This is how the evil gets permanent access to John’s emails.
Many practitioner-run project email systems have a defense against this kind of breach. The system sends a daily access summary to users. If John reviewed his access summary, this compromise would have been identified within one day. John would then change his password on a clean computer and review and remove any forwarding rules.
The daily access summary lists the accesses to the email account over the past 24 hours. It includes the IPs from which the account is accessed and in what way, and whether the access was successful. The most likely IPs would be your work IP (if you check email from work), your home IP, and your mobile device IP (if you check email from your mobile devices). Any IP that is outside of this set is suspicious, especially any IP from another region or country. You can use whatismyip.com to find out your current IP of your phone or your computer.
If John was vigilant he would have noticed a successful access from an unrecognized IP that used the web interface. This would be enough to alert John that his email password had been compromised and the email account settings may have been changed.
Let’s assume John failed this test also. The evil would be able to receive all of John’s emails from this point on. The evil will watch the email threads and conversations to gather information and look for opportunities to compromise other people’s computers via email malware and social engineering.
Since John and David had been discussing residence applications, the evil sent an email to David from John’s email account with a malware attachment.
Keep Your Devices up to Date
As a general rule, do not open email attachments unless you are sure it is safe to do so.
But how do you know if it is safe to do so? The simplest and most effective way is to call the sender to confirm. Please do not use email to confirm, as the sender’s email account may have been compromised by the evil already.
David discussed residence applications with John before and then John sent an email with a document called “List of documents needed for residence application.” It would be easier to discard messages that were not expected or not relevant or from an unknown sender, but this one was kind of expected and definitely relevant and from a trusted sender. The evil created a perfect socially-engineered trap by leveraging prior knowledge of the ongoing discussions between the victims.
Are we doomed?
Not yet.
The right thing to do here is to call the sender to confirm they sent the document before opening it. John would then realize that his email account had been compromised. He would change his password on a clean computer and review and remove the forwarding rule.
Let’s assume David did not call John and fell into this trap. He opened the document and triggered the embedded malware. What happens next would depend on the malware and our defenses on the device.
If the malware was targeting a known vulnerability in the operating system (OS) or in the application (Word, PDF reader, Java, etc.) it would fail to cause damage if the OS and applications were up to date.
This defense is effective and easy to implement (by diligently keeping the OS and applications up to date) but many people fail to do this.
We should install updates for the OS and applications as soon as we are notified. Do not delay. Most applications (browsers, PDF readers, Java, etc.) have automatic update mechanisms. Turn them on and use them.
Windows has the Windows Defender as part of the OS. It is very good. Remove any other trial security software that came with the PC, and use the built-in Windows Defender. It will be updated as part of the OS updates.
Mac OS has Gatekeeper, XProtect, and the Malware Removal Tool. They are very good. There is normally no need to use other antivirus tools for Mac.
Remove any applications that you do not use from your devices to avoid them being targeted by any future malware.
David would have been fine if his device was up to date and the malware was targeting a known vulnerability.
What if the malware is targeting an unknown vulnerability (called a 0-day)? The vulnerability is unpatched and anti-malware programs have no way to detect it.
Are we doomed?
Not yet.
Standard User for Most Activities on Devices
There are at least two types of users on a computer: administrator and standard user.
If you login as an administrator, you can do anything on the computer. That sounds nice but the malware you triggered will have the same rights. The malware can do anything on your computer if it is triggered by an administrator.
If you login as a standard user, you can do most of your tasks fine but you cannot write to the system folders. This sounds limiting but the malware you triggered would not be able to create nasty stuff in the system folders. This is good protection as normally you do not need to write to the system folders, and malware triggered by you will be severely limited as to what damage it can cause.
By simply logging in as a standard user, certain malware will fail to cause damage even if it targets an unknown vulnerability.
The good news is that in modern OSs (Windows and Mac) the user is operating in standard user mode, even if the user is an administrator. If you need to do something that requires the administrator rights, Windows will ask you to confirm, and MacOS will ask you to enter a password. This is your opportunity to stop the malware from installing itself or running as an administrator.
In David’s case, he was trying to open an attachment from an email and got prompted to allow changes to the system. This was his chance to say “No,” as opening a document should not make changes to the system.
To avoid quickly clicking Yes without reading and thinking it is recommended to log in as a standard user. If running as a standard user, the system would ask for the password of an administrator instead of a simple Yes/No question. This increased friction will hopefully help us pause and think when prompted for action.
So if you see a prompt on Windows or Mac asking you to enter a password or allow an application to run, please read the prompt carefully. If it is not your intended action, please do not enter the password or allow it to run, as it could indicate malware.
Similarly if you see a prompt on your phone or tablet asking you to allow a certain action or app installation, please read carefully. If it is not your intended action, please do not click anything. Use Force Quit to close all running apps to remove the prompt.
As a general rule, when the system, an email, or a text message asks you to do certain operations, please pause and think. If it is not your intended action, please do not do it.
An example: A coordinator was negotiating the contract with a theater and received an email with an attachment called “Contract draft.xlsx” and the phone rang at the moment when she was thinking about whether to open the attached file. While on the phone she opened the file and realized that she had made a mistake, as the sender was not that theater. The attached file did contain malware. However, she was logged in as a standard user and the virus failed to cause damage to her system.
Only Run Trusted Applications
By simply logging in as a standard user, certain malware will fail to cause damage even if it targets an unknown vulnerability.
Certain malware, not all malware? Yes. Some advanced malware may be able to elevate a standard user to an administrator and cause damage to the system.
Are we still doomed?
Not really.
Our defense for this will be application whitelisting: Only run trusted applications.
The most advanced malware in our story targets an unknown vulnerability and has the capability of privilege escalation. It will not run if it is not in our list of trusted applications and it cannot cause damage on our devices.
Application whitelisting can be implemented on Windows using AppLocker and Smart App Control in Windows 11.
MacOS has three settings: App Store Only, App Store and Identified Developers, Open Anyway. The first setting, App Store Only, should be used most of the time. It is OK to use the second setting to allow apps from Identified Developers. But the digital certificates for the Identified Developers could be stolen so the second setting does carry some risk. The third setting should not normally be used.
The principle of “only run trusted applications” is the ultimate defense. The malware, no matter how advanced, will not be on the list of our trusted applications. As long as we do not run it, it will not be able to cause any damage. Similarly if we do not fall for social engineering traps, malicious email attachments, and links, and malicious text messages, and malicious QR codes will not cause damage to our devices.
Let’s assume David failed to implement this defense and the malware succeeded on his device. This malware will capture his passwords for all his online accounts, including his secure email account. Of course the evil will log in to his account to set up a forwarding rule and send a malware attachment to John, now titled “My stories of persecution in China.” If John fell into this trap by opening this document his computer might be fully compromised. The cycle would continue.
After monitoring John’s online activities for some time the evil decided that it might be worth a trip to John’s home. With the information gathered earlier, the evil broke into John’s home and took laptop computers, external hard drives, and USB flash drives.
Protect Data on Devices with Passcode and Encryption and Backup
Have we lost everything at this point?
Not if we have protection in place for our devices.
Enable passcode and auto data erasing for mobile devices.
For computers, Windows has BitLocker, PGP Disk, and VeraCrypt for whole disk encryption. MacOS has File Vault. Turn on encryption on all devices. Encrypt data on external hard drives and flash drives. The evil will not be able to get any information even if it gets our devices.
However if we lose our devices our work will be severely impacted even if the evil does not get access to the information on the devices. It would still be a big loss for us. To avoid this kind of loss (interruptions to work), we should configure automatic encrypted data backups to remote sites or cloud services for all devices. In the case of lost, stolen, or damaged devices we will be able to restore the data from backup on to replacement devices and get back to work quickly.
The attacks we have talked about so far are the attacks from the evil, not general attacks from the Internet. We only touched on a few most common ones. We mentioned some defenses in concept. The implementation details can be found through more discussion on the topic.
General Technical Details
Data Backup
We will talk about three different types of backup, all of which are indispensable for different protection.
Backup on the Same Disk
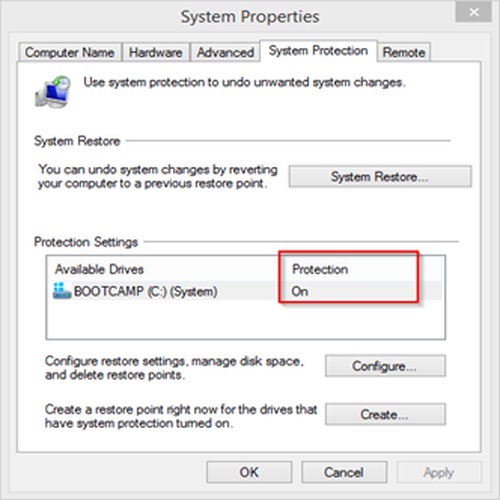
The first level of protection is called System Protection, which is available on Windows. It is also called System Restore Points. A snapshot of the disk is saved on the same disk using Volume Shadow Copy. Enable System Protection so that you can recover deleted files or earlier versions of the same file. In case of a failed Windows update or unbootable system due to corrupted system files it is possible to recover the files and make the system bootable again.
Press the Windows key and type “system” and click “System” in the search results, then click System Protection on the left to launch the window:
Example: Important files got deleted by mistake. An operator at the printing shop deleted the printing template files by mistake. The printing cannot proceed without the template files. Since the deletion was performed through a program the files could not be recovered from the Recycle Bin. The technical support person was able to restore the template files from the system restore points and the printing operation was resumed in time to finish printing by the early morning.
Example: The system became unbootable after software installation. The system entered a reboot loop after some software installation. The technical support person pressed F8 to stop the system from automatic reboot and checked the error code. It was determined that the system registry was damaged. Since this machine itself was unbootable, the technical support was able to recover the system registry before the software installation by attaching the hard drive to a working computer. The system was able to boot normally afterwards.
System Protection is valuable but it does not protect against hardware failure. You will lose both the Restore Points and the data in case of a hard disk failure. So we need to backup data to a different disk.
Backup to a Different Disk Locally
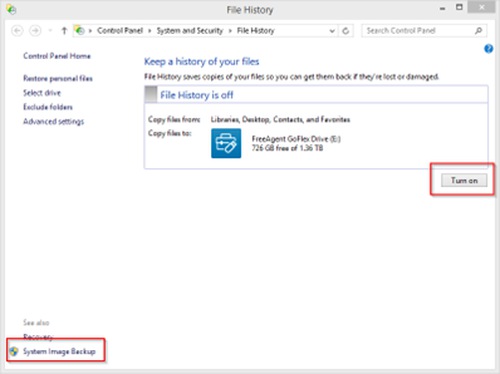
To protect against hard disk failure you will need File History on Windows and Time Machine on Mac to backup your files to a dedicated external disk. Use a blank disk to avoid data loss for the initial setup.
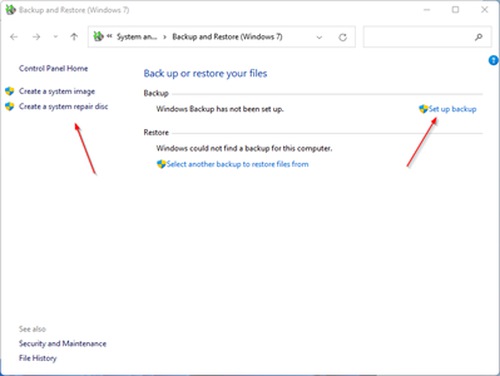
You can also create a system image backup and a recovery media to restore your OS to an earlier backup.
Mac: search for Time Machine in Spotlight and launch Time Machine to start configuration. Time Machine backup can be used to restore the entire system or individual files.
Windows: Press the Windows key and type “file history” and click “File History” in the search results to get started. File History does not include a system image. Please make sure to create a system image separately (can be scheduled) so that you could restore the whole system to an earlier point.
Please keep the backup disk connected to your computer so that the changes you make to your files will be backed up automatically. If you do it manually, and only occasionally, it is easy to forget to do it. Please establish the habit of keeping the backup disk connected to the computer at all times and let Time Machine or File History do automatic and continuous backup.
Example: Disk failure without warning. A computer was turned off for the night. It showed that the OS disk was not found the next morning. It turned out that the SSD disk for the OS had failed without warning. There was a daily system image backup at 9 p.m. to a second disk. The backup from the previous night was restored to a new SSD and the user was able to continue her work without significant data loss (lost work between 9 p.m. and 12 a.m. which can be avoided by a continuous File History backup).
Modern devices use SSD disks. SSD disks are faster and more reliable than traditional disks but they still fail eventually, often in a catastrophic way (with no way to recover data) and without warning. For any device with a SSD disk there must be a continuous backup in place to protect the data on the device.
This setup requires that an external disk be connected to the computer, thus it is a local backup. There is a risk of losing both the computer and the backup disk in the case of a break-in or house fire. A remote backup is needed to protect against this risk.
Remote Backup
Remote backup can protect against the risk of losing the device and the backup disk at the same time. You can use a complete backup service such as Backblaze to create encrypted backup files, or Duplicati, which creates backups stored on your choice of remote locations (e.g., your own FTP server, or cloud storage such as Backblaze B2, One Drive, Google Drive, Amazon S3, etc). Duplicati is free and open source: https://www.duplicati.com/.
Protect Data with Encryption
Example: House break-in. In early 2005 the evil broke into a practitioner’s home in Atlanta and took his computers and external disks. The computer disk was encrypted.
If your computer or disks fall into the wrong hands, the information stored in them can be stolen easily, unless you encrypt them.
You have to remember and retain your encryption password. Otherwise, no one will be able to access your data. Every time you boot your computer or access your external disks, you have to enter your encryption password.
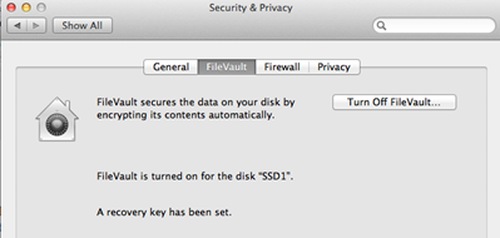
MacOS has a program called FileVault to encrypt disks. Search for FileVault in Spotlight to get started. Make sure you save your recovery key in a safe place.
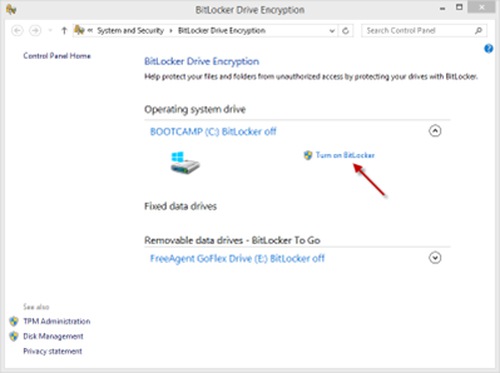
Windows BitLocker disk encryption is available in the professional or business editions of Windows. Unfortunately it is not available in the Home edition. Please consider upgrading your Windows edition to get BitLocker if you need this protection. You can upgrade without reinstalling Windows by purchasing a license key from the Microsoft Store. You can also use VeraCrypt on Windows, which is free and open source: https://www.veracrypt.fr/code/VeraCrypt/.
On the proper edition of Windows, press the Windows key and type “bitlocker” and click “Manage BitLocker” to get started. You can encrypt both internal disks and external disks. Click “Turn on BitLocker” and follow the instructions.
Use a Password Manager
The best way to manage passwords is to use a password manager such as KeePassXC for Mac OS and KeePass for Windows.
You only need to remember one strong password to open the password manager itself. The password manager will generate strong unique passwords for everything else. This is the only way to avoid using weak passwords and using the same passwords in multiple places, and forgetting passwords or forgetting where to find a password.
When you start the password manager for the first time, it will create a new blank database for passwords and ask you to provide a strong master password. You can then create new password entries for your existing passwords. From this point on, create a new password using the password manager for each site requiring a password.
This password database file is extremely important to you. The best way to protect it is to use a cloud storage such as Dropbox, One Drive, Google Drive, etc. It is protected by strong encryption so it is OK to store it in the cloud. The file size is tiny, so the free tier of any cloud storage will be more than enough. If it is in a cloud storage area it will be available on most of your devices and will be synchronized automatically on all of your devices. To avoid potential synchronization conflicts it is best to edit on one device only.
KeePass: https://keepass.info/ WindowsKeePassXC: https://keepassxc.org/ Windows, Mac, Linux
Email Client Setup
Please do not use something like Gmail for sensitive messages. Instead use internal project email services. Many of the internal project email services send an access summary to you automatically each day which you should review every time you check your email. This enables you to be notified should your account be accessed by the evil.
Archive your emails on a secure computer. Do not leave email messages on an email server, because if you do, and if your email password is stolen, all your messages can be downloaded by the evil.
Download and archive your messages on a secure computer with POP3 (instead of IMAP) using an email client such as Thunderbird or Apple Mail. This will preclude accessing the email account from your other devices such as your smartphone however (IMAP enables shared access).
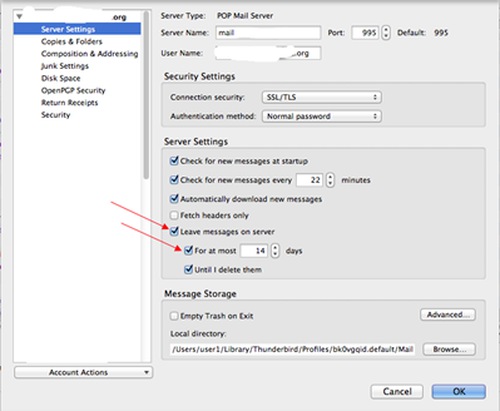
If you also want to check your email with a mobile device (such as an iPad), set up your email client such that your messages will be kept on the server for at most two weeks, and set up your mobile device to use IMAP to access your emails. (IMAP mirrors your email messages on the email server, while POP3 downloads your messages onto your local computer.)
Below are some screenshots from Thunderbird. When you add an email account, select POP3, and switch to manual setup mode. The POP3S port is 995, the SMTPS port is 994.
Other Measures
Example: Initial infection of Stuxnet. The computers in the Iranian nuclear facilities were not connected to the Internet so direct online attacks from the Internet were not possible. The enemy dropped some small USB thumb drives in the parking lot of the facilities. Some workers picked up the USB thumb drives from the parking lot and plugged them into their work computers. The virus on the USB thumb drives infected the computers and propagated to the control hardware of the centrifugal machines. The virus changed the spinning speed of the centrifugal machines and caused widespread damage.
Please do not insert unknown USB flash disks, CDs or DVDs into your computer. Please do not connect unknown FireWire or Thunderbolt devices to your computer.
Use the uBlock Origin add-on for browsers to prevent malicious links and code from the advertisement network.
Please do not use Simplified Chinese as the default language for Apple devices. If you do, Apple will store the information from your devices on the iCloud servers in China. If you have to use Chinese for your Apple devices, use Traditional Chinese (Taiwan, not Hong Kong).
Mobile Devices
Source: the NSA Mobile Devices Best Practices as of 7/28/2020
Some practices are applicable to PC or Mac
Bluetooth: Disable Bluetooth when you are not using it. Airplane mode does not always disable Bluetooth.
Wi-Fi: Do not connect to public Wi-Fi networks. Disable Wi-Fi when not needed. Delete unused Wi-Fi networks.
Control: Maintain physical control of the device. Avoid connecting to unknown removable media.
Case: Consider using a protective case that drowns the microphone to block room audio (hot-miking attack). Cover the camera when not using.
Conversations: Do not have sensitive conversations in the vicinity of mobile devices that are not configured to handle secure voice.
Passwords: Use strong lock-screen pins/passwords: a 6-digit PIN is sufficient if the device wipes itself after ten incorrect password attempts. Set the device to lock automatically after five minutes.
Applications: Install a minimal number of applications, and only ones from official application stores. Be cautious of the personal data entered into applications. Close applications when not using.
Software updates: Update the device software and applications as soon as possible.
Biometrics: Consider using Biometrics (e.g., fingerprint, face) authentication for convenience to protect data of minimal sensitivity.
Text messages: Do not have sensitive conversations on personal devices, even if you think the content is generic.
Attachments/Links: Do not open unknown email attachments and links. Even legitimate senders can pass on malicious content accidentally or as a result of being compromised or impersonated by a malicious actor.
Trusted accessories: Only use original charging cords or charging accessories purchased from a trusted manufacturer. Do not use public charging stations.
Location: Disable location services when not needed. Do not bring the device with you to sensitive locations.
Power: Power off and on the device weekly.
Modify: Do not jailbreak or root the device.
Pop-ups: Unexpected pop-ups like this are usually malicious. If one appears, forcibly close all applications (iPhone: double click the home button or swipe up from the bottom of the screen and pause slightly in the middle of the screen then swipe up to close or Android: click recent apps soft key).Source: https://media.defense.gov/2020/Jul/28/2002465830/-1/-1/0/Mobile_Device_UOO155488-20_v1_1.PDF
Mac OS
Network Configurations
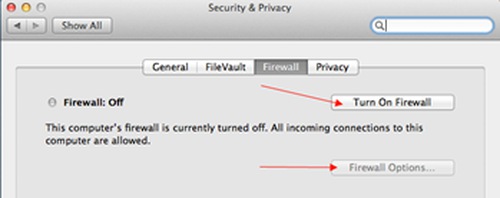
Turn on your firewall to block all incoming connections. Search for firewall in Spotlight to get started.
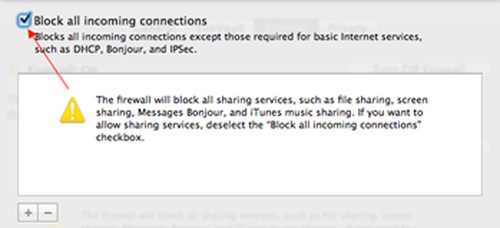
Click Firewall Options and check Block all incoming connections.
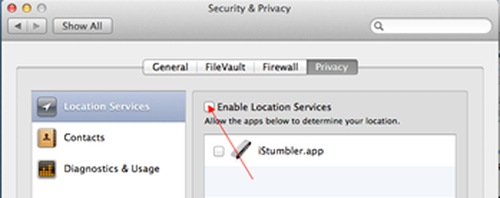
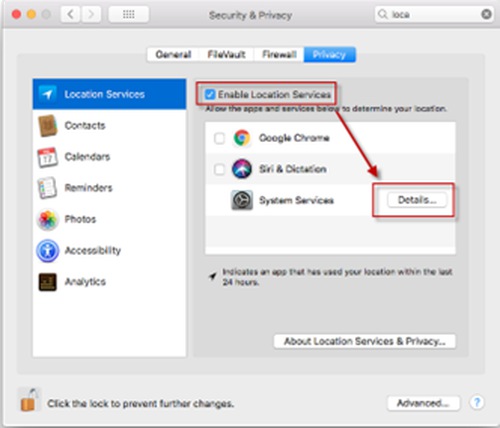
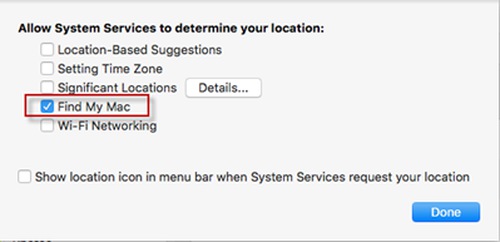
Turn off Location Services if you do not wish to use Find My Mac.
If you wish to use Find My Mac, you need to turn on Location Services, but uncheck all other items.
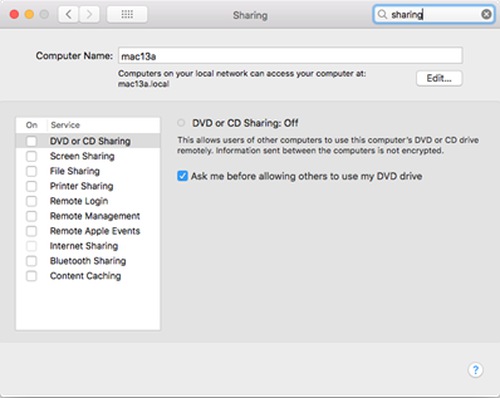
Turn off File Sharing, Screen Sharing, Remote Login, etc, via System Preference > Sharing or search for sharing in the upper right corner box. They will be turned off when you choose Block All Incoming Connections in Firewall Options.
Windows
Network Configurations
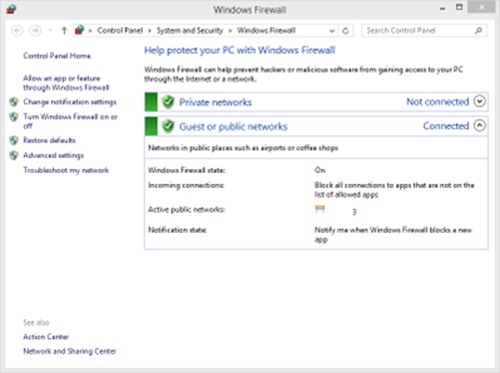
Press the Windows key and type “firewall” and click “Windows Firewall” in the search results to get started.
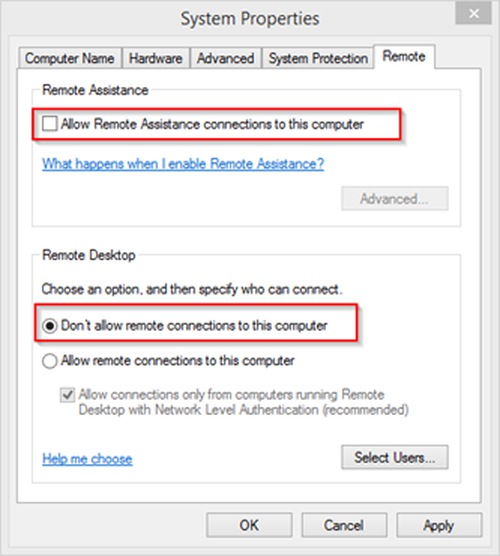
You can turn off Remote login if you do not need to access this computer remotely. Press the Windows key and type “system” and click “System” in the search results. Click Remote Settings.
Windows 11 Security Features
If you are using Windows devices please upgrade to Windows 11 if possible. This is consistent with the principle of keeping the OS and applications up to date. There are significant improvements in security for Windows 11 devices. Some improvements are in the OS. Some improvements are based on the higher hardware requirements such as TPM2, etc.
We mentioned earlier that the ultimate defense is “only run trusted applications.” The Smart App Control in Windows 11 greatly simplifies the implementation of this defense.
Ransomware encrypts user files and demands ransom for decryption. Since ransomware would encrypt files that belong to this user, no administrative rights are needed for this encryption operation. Logging in as a standard user cannot prevent ransomware from causing damage. Windows 11 added Controlled Folder Access to allow only trusted applications to modify the files in these protected folders. Since ransomware will not be on the list of trusted applications, it will not be able to encrypt the files in the protected folders.
Windows 11 has Application Isolation to run dangerous files and web pages in a container. The system would be protected from harm even if the files and web pages are malicious. By default the Windows 11 Application Guard will open Word files, PowerPoint files, Excel files, Microsoft Edge in protected containers.